
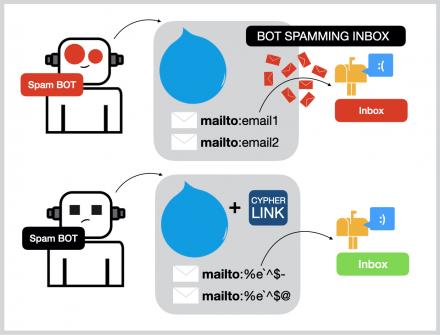
The technology protects both parties from fraud while preserving the security of transactions through the use of cryptographic authentication methods. Customers have choices of varied cryptocurrencies based on their privacy requirements and technical requirements. CipherLink is a lightweight, high-performance communication library designed to provide end-to-end encryption for secure data exchange between clients and servers. Leveraging industry-standard AES-GCM encryption, CipherLink ensures the confidentiality and integrity of messages transmitted over the network.
Issues For Cypher Link

Layer after layer of security ensures that your information stays protected. We understand the importance of quality and customer satisfaction, which is why we stand behind our products with a robust guarantee. If you’re not completely satisfied with your purchase, simply reach out to our friendly customer support team, and we’ll work to resolve the issue to your satisfaction. Cypher Link is a decentralized crowdfunding platform designed to empower indie developers by facilitating transparent and cross-chain funding transactions. Built using ThirdWeb SDK, ReactJS, Ethers, and TypeScript, Cypher Link aims to revolutionize the way developers connect with supporters and receive funding for their projects through the use of cryptocurrency.
- Distributed server networks across various geographies are managed by administrative groups to achieve operational continuity and immunity against focused attacks.
- Save time by translating entire documents or message sets at once.
- Return the union of all query results, including duplicate rows.
- The point() Cartesian 3D function returns a 3D POINT in the Cartesian CRS corresponding to the given coordinate values.
The datetime.fromEpoch() function creates a ZONED DATETIME given the seconds and nanoseconds since the start of the epoch. The trim() function returns the given STRING with leading and trailing whitespace removed. The toUpper() function returns the given STRING in uppercase. The toLower() function returns the given STRING in lowercase.
Final Thoughts On Cypher Market
Cypher also stands out for exclusive offerings like custom hacking services, malware, and sought-after data dumps, reinforcing its status as a trailblazer in the darknet market arena. Produce complex encrypted messages using keyword-based polyalphabetic substitution for enhanced security. Create personalized coded messages using unique substitution patterns or custom alphabetic arrangements. AI-powered system automatically detects common cipher patterns.
Super Market
Buy and sell Dota 2 items on the Steam Community Market for Steam Wallet funds. Shares of Good Works rose cypher market to cypher market after markets opened for trading on Friday. Yonkers montessori academy teachers notebook Your contribution will help provide adaptive equipment, rehab equipment and.

Banking & Financial Services Specialization
Launched after the takedown of AlphaBay in 2021, Abacus Market has rapidly risen to prominence. It features over 40,000 listings including narcotics, counterfeit items, hacking tools, and stolen data. The marketplace is well-known for its bug bounty programs and robust security mechanisms, including mandatory 2FA.
Integrating Cryptocurrency Payment Solutions

Additionally, the page’s title is a triangle symbol “△”, and an eye emoji as its favicon “👁️”. Multi-layered defense against sophisticated cyber threats with real-time monitoring. Good community forums are the most reliable sources of verified access information. Never use access links from unauthorized websites or social media. Cypher Market relies on advanced technical infrastructure to provide anonymity and good service. The site is only available on the Tor network`s hidden services using onion routing for every connection.
Fixed-length Patterns
- Shop with confidence at our cypher darknet link online store.
- The point() Cartesian 2D function returns a 2D POINT in the Cartesian CRS corresponding to the given coordinate values.
- If you are not satisfied with your purchase, you can return the item for a full refund or exchange.
- You can shop with confidence knowing your cypher darkweb url is safe with us.
Understanding the intricacies of this challenge on HackTheBox will elevate your cybersecurity skills. Cypher introduces you to the world of cryptography and graph database vulnerabilities, including various query techniques. Mastering Cypher involves deciphering encrypted messages, exploring directories, and exploiting server weaknesses. By delving into this realm, you’ll enhance your ability to identify and mitigate potential security threats.
As Charlie Sheen and Oliver Stone do not know each other in the example graph, this MERGE query will create a KNOWS relationship between them.The direction of the created relationship is left to right. As of Neo4j 5.20, specifying a property of an entity (node or relationship) by referring to the property of another entity in the same MERGE clause is deprecated. Grant SHOW PRIVILEGE privilege to list privileges to the specified role. Grant SHOW ALIAS privilege to list aliases to the specified role. Grant CREATE ALIAS privilege to create aliases to the specified role.
Create a node property uniqueness constraint on the label Person and properties name and age. An error will be thrown if an attempt is made to create the same constraint twice. If any node with that label is updated or created with a name and age combination that already exists, the write operation will fail. Create a node property uniqueness constraint on the label Person and property name. Using the keyword IF NOT EXISTS makes the command idempotent, and no error will be thrown if an attempt is made to create the same constraint twice.
Enables the specified role to use elevated privileges when executing all user defined functions. Revoke IMPERSONATE privilege to impersonate all users from the specified role. Deny IMPERSONATE privilege to impersonate the specified users (user_name1 and user_name2) to the specified role.
Archetyp Market
Our website uses the latest encryption technology to protect your cypher url data, and we never share your information with third parties without your consent. You can shop with confidence knowing your cypher darkweb url is safe with us. We offer a variety of shipping options, including standard, express, and expedited delivery. Depending on your location and the shipping method you choose, your order can be delivered within cypher mirror to cypher darknet url business days. A node represents an entity or discrete object in your graph data model.



