
Thanks to the evidence Stefan and his team gathered on the Robertsson brothers, Swedish courts were able to convict them of selling drugs on the darknet. After conducting undercover purchases from Robertsson on Flugsvamp to confirm he was still selling drugs, Stefan and his team received warrants to tap Robertsson’s phone, put a GPS tracker on his vehicle, and watch his house with cameras. By placing more test orders with him and observing his online and offline behavior, they were able to intercept more of his packages and build their case further. Manual monitoring of the dark web is inefficient and risky due to the sheer volume of data involved.
Specialized Marketplaces
The market started in 2021 in Canada and features both international and Canadian users. The market offers things like malware, fake documents, and financial fraud services. This market is not open to the general public and is subject to a thorough vetting process to ensure its security. In fact, WeTheNorth is more of a private club than an open market – something its operators want.

Darknet Market
On the one-year anniversary of Hydra’s seizure, Flashpoint explores how threat actors have adapted to fill the market’s void and fuel their illicit aims—from narcotics transactions to money laundering. Silk Road was once the most well-known dark web marketplace, but after its shutdown, many new markets took its place. Today, buyers and vendors look for reliable alternatives that offer security, escrow protection, and a strong vendor community. Some markets have services related to cybersecurity, while others might list more controversial items. This secure setup is useful for those who want to avoid government surveillance or keep their personal information safe from online threats. Our regional data reveals that most people buying stolen credit card data on UNICC are from North America (after Global), while most of those selling it are from China.
Products & Services
Market takedowns create temporary disruptions, but they rarely dismantle entire networks. Sophisticated players shift operations, adopt new aliases, and resume business within weeks. Litecoin, Zcash, and Dash also see usage, though Monero and Bitcoin dominate the dark web. Some marketplaces have even mandated Monero-only transactions, underscoring a strong preference for privacy-focused coins over traceable ones.
Unique Features
Nemesis Market also saw its demise in March, when German authorities seized its infrastructure, along with $102,000 in cryptocurrency. Hudson Intelligence assists law firms, businesses, public agencies and investors with cryptocurrency investigations and due diligence. Every investigation is led by a Cryptocurrency Tracing Certified Examiner (CTCE) and Certified Fraud Examiner (CFE). If you would like to discuss a potential investigation, please complete the form below. He recommends verifying market employees carefully, and to weed out law enforcement infiltration through barium meal tests.

Cryptocurrencies have replaced fiat currencies as the default medium of exchange on the dark web. Bitcoin continues to lead as the most widely accepted digital currency due to its high liquidity and global acceptance. However, its transparent blockchain has prompted users to shift toward more private alternatives. Others are looking for stolen data, hacking services, or even banned books and political content. By supplying stolen data, these dark web links fuel many online scams and identity theft operations, playing a critical role in the darker aspects of the internet. These sites cater to cybercriminals seeking valuable data, such as credit card numbers, login credentials, and personal information.

This browser enables access to websites with .onion domain extensions, which are specific to the Tor network. These addresses cannot be resolved by conventional DNS servers, contributing to the hidden nature of darknets. However, overall the sector has fragmented somewhat from the days when Silk Road, AlphaBay, Wall Street Market and Hydra ruled the roost. Today, no single player is dominant like these marketplaces were before their takedown, with administrators preferring to specialize in particular types of goods and services. STYX Market focuses specifically on financial fraud, making it a go-to destination for cybercriminals engaged in this activity. To expand their reach, some marketplaces established parallel channels on Telegram.
- While these hidden networks can be used for legitimate purposes, they are equally significant as vectors for cybercrime and illicit activities.
- Some marketplaces have even mandated Monero-only transactions, underscoring a strong preference for privacy-focused coins over traceable ones.
- As we mentioned previously, while shops specializing in drugs are the most popular type of darknet market, they’re not the only type of darknet market to achieve consistent sales.
- The last several years’ examples include Silk Road, AlphaBay, Wall Street Market, and Hydra, most recently.
Versus Market (Best For User Reviews & Vendor Ratings)
Cryptocurrency provides both financial innovation and potential for criminal use, posing problems to regulators and law enforcement. Blockchain transparency facilitates the tracing of transactions but is exploited by the veil of pseudonymity. Bitcoin and Ethereum are traceable platforms that can facilitate forensic analysis, but privacy coins such as Monero and Zcash ensure that the transactions become irretrievable and tracing impossible.
Cyble Strato Cloud Security
In this post, we’ll walk you through the top 10 dark web marketplaces that you need to watch for potential threats to your organization. As far as financial recourse for victims, some banks and insurance companies have provided payouts and will include those funds as damages in lawsuits against Genesis Market cybercriminals. As for Genesis Market cybercriminals located in the Netherlands, three have already been convicted and received prison sentences considered severe for that jurisdiction. The third convicted cybercriminal — the biggest Dutch user and the number 10 user worldwide — received a four-year sentence.
Strengthening regulatory frameworks, enforcing compliance measures, and improving transaction monitoring are essential to reducing these risks. Cryptojacking exploits victims’ devices for unauthorized cryptocurrency mining, leading to performance issues and financial losses. Fake wallets mimic legitimate apps, tricking users into depositing funds or revealing private keys. Fraudulent exchanges lure investors with promises of high returns or low fees before stealing their money.
Incognito Market runs 20,000+ listings and $2.8 million monthly trades with BTC and XMR, holding a 5% market stake. Its 10,000+ users and 800+ vendors rely on 2FA and escrow security for private cryptocurrency trading. Global law enforcement agencies face mounting challenges in tracking and dismantling dark web operations. In 2025, authorities have increased efforts to identify illicit transactions, monitor suspicious wallet activities, and take down infrastructure supporting criminal trade.
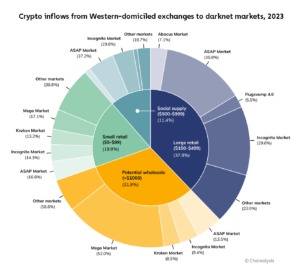
In 2023, the New York Police Department (NYPD) Intelligence Bureau, which predominantly handles counter terrorism cases, received a tip about two people in New York City involved in manufacturing and selling ghost guns. Using a series of search warrants and subpoenas, the NYPD found the suspects’ online raw material purchases, and uncovered a crypto dimension to the case, not publicly shared until now. Suspects were exchanging large sums of fiat for cryptocurrency by transferring cash into a mainstream CEX account and buying BTC, which they used to purchase stolen credit cards and identities from fraud shops on the dark web. The Reactor graph below shows five purchases made to fraud shops, four of which passed through intermediary addresses.
Budget, Financial Reporting, Planning And Performance
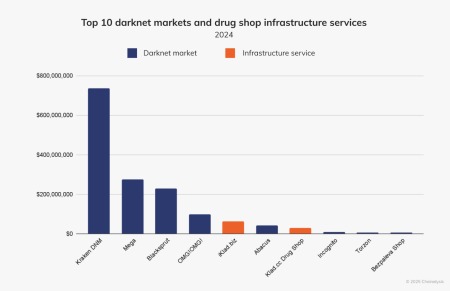
The entity “DNM Aggregator” that appears within each category refers to a service we’ve identified as being in control of multiple, disparate darknet markets. Throughout the history of the darknet market ecosystem, at different turns one marketplace has typically played the dominant role. The last several years’ examples include Silk Road, AlphaBay, Wall Street Market, and Hydra, most recently.
These collaborations increase the scope and impact of attacks, often targeting infrastructure, defense systems, and financial institutions. Rivalries between nation-state actors have also spilled into the dark web, with turf wars emerging between different sponsored groups over control of marketplaces and services. Telegram channels, encrypted messaging apps, and invite-only forums support additional layers of communication and product distribution. Vendors advertise products through these channels and redirect buyers to secure purchasing portals.



