
However, be careful when using the Tor Browser to access the dark web. The dark web is a dangerous place, and all bets are off on your safety. This encrypts your internet traffic using your VPN’s servers, protecting against outside parties monitoring all of your device’s internet activities. Whonix uses Oracle Virtualbox to run two virtual machines (VMs) on top of your currently installed OS (Windows, Linux, or Intel-based macOS). The Whonix Gateway VM handles Tor processes, and the Whonix Workstation VM runs user applications on an isolated network.
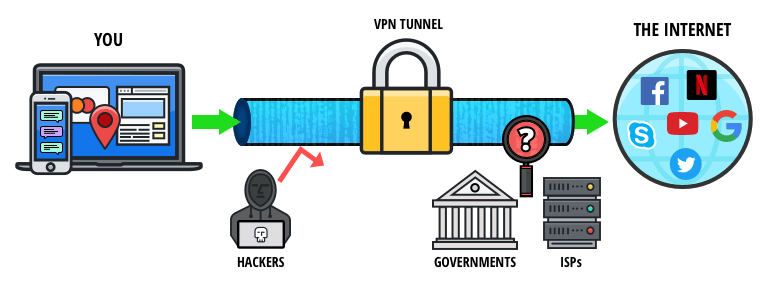
VPN stands for virtual private network, and it acts as a security bubble for communications from your device. A VPN automatically encrypts your data as soon as it leaves your device through the VPN server. This means your private information, location, and any communications you send are hidden and protected. The difference between the surface web and the deep web is that pages, websites, and content on the deep web are only accessible to authorized users with the appropriate credentials. In other words, these are pages that aren’t indexed and therefore can’t be found by a typical search engine. A large portion of activities on the dark web involve illegal content, transactions, or services.
How To Remain Safe When Using Darknet Browsers
This provider’s performance is top-tier, with full Tor Over VPN support to make things simpler. Connect to ANY of its 3,000+ servers, open Tor, and do your magic! ExpressVPN’s intuitive apps work on up to 8 devices at a time, ensuring protection for the entire family. It also has 10 simultaneous connections, support for all devices, and server obfuscation that works in China. These websites will now work without issues, as the VPN hides the exit node and makes your traffic look inconspicuous.
Best Dark Web Browsers And Search Engines
However, keep in mind that the dark web is not organized like the regular internet. Instead of search engines, you’ll need to rely on directories or specific .onion links. Tor protects your identity inside its network, but it doesn’t hide everything. Your ISP still knows you’re using Tor, and entry nodes can see your real IP address. A VPN adds protection before Tor, closing these gaps without breaking access to .onion sites.
Types Of Dark Web Sites (and What Really Goes On There)

Responsible use protects your privacy while staying within the law, so it’s a safe place to browse for real privacy reasons. However, this does not provide any extra security for your device or information. The Tor network was created by the US military in the 1990s for anonymous communication between spies over the internet.
Enable Strong Security Settings
- A dotonion web address, which is exclusively accessible via Tor Browser, protects the identity of both websites and visitors through complex, encrypted, and anonymous connections.
- As search engine crawlers do not catalog these pages, you would need to know the exact link to access a website in this area of the internet.
- This feature offers a more direct and potentially more trustworthy way to find the onion versions of legitimate websites.
- VPN stands for virtual private network, and it acts as a security bubble for communications from your device.
- Ahmia is a search engine that aims to make searching the dark web more accessible and safer.
Unfortunately, it’s slower than NordVPN and ExpressVPN but overall, its performance is admirable in practice. While you can visit the obscure part of the internet without a VPN, it’s better to go with one. Here are our favorite choices that work well and support Tor Over VPN perfectly. This method is far more complex but we’ll still explain it for those too curious. As opposed to the previous situation, here, you’re first connecting to Tor and then the VPN.
Verified Social Channels And News Sites
Always use an abundance of caution when interacting with anything or anyone on the dark web. To access a dark web address, you must use a VPN and a suitable browser (it should be Tor). The aim is to reduce your online footprint as much as possible, anonymize your traffic, and disguise your location.
How To Access The Dark Web
Make sure you have a reputable antivirus running on all your devices. Use security software like Avast One to help protect against online threats. The dark web is full of cybercriminals who know curious users are checking out Tor. Some scammers prepare fake downloads infected with viruses and other malware.
Join millions of users who trust ForestVPN for privacy and unrestricted internet access. The dark web can be dangerous due to the presence of scams, cybercriminals, and malware. Users should exercise caution and follow safety practices to minimize risks. For many of us, the dark web represents an enigmatic corner of the internet, often shrouded in myth and misunderstanding. Yet, beneath its shadowy veneer, it offers both legitimate and illicit opportunities, making it a topic of fascination and concern. As we delve deeper, we’ll explore the dark web’s true nature, its uses, and why it merits our attention.

Can I Be Tracked While Using Tor?
Many people install a VPN as well, but then you’re putting your trust in an additional third party to not track your activities or report them to anyone else. However, there are plenty of legal and legitimate online activities that require privacy and anonymity. The dark web is used by journalists, whistleblowers, and political activists who need the protections that it offers.
You should never trust websites and forums on the dark web with your personal information. You can use these dark web investigation tools to check if your company’s data is available on the dark web. If you decide to venture into the dark depths of the deep web, make sure you’ve bolstered your device’s security with powerful privacy and security tools that can defend against dark web threats. From real-time alerts vetted by Cyble’s Security Operations Center (SOC) to AI-driven risk tagging, Cyble enables faster, more informed response decisions. Its deep insights into cybercrime forums, compromised card databases, and exposed assets give security teams a critical edge. Choosing a dark web monitoring tool requires a lot of factors, including price, availability, and many other things.

In darknet mode, you can select friends on the network and only connect and share dark web content with them. This enables individuals to form groups and only share content in a highly anonymous network of darknet users who they know. Since you’ve now installed the Tor browser, you can safely browse dark web websites and other (previously) hidden websites.



