
Opennet connections are easier to use, but darknet connections provide more security against attackers on the network. I2P can only be used to access hidden sites that are only available on the I2P network. Supreme Court will allow the FBI to search and seize any computer that’s using the Tor browser or VPN. Rule No.41 allows a federal judge to issue a search and seize warrant for any person who is using anonymity software like Tor. The last thing you need to do is to start researching vendors and determine what marketplace is a possible vendor to buy the products from. Click on “Safest.” As you’ll see, JavaScript and a few other features will be automatically disabled on all sites.

Useful Links
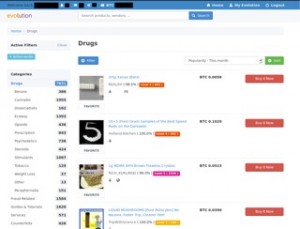
Valued at approximately $15 million, Abacus Market is one of the most lucrative platforms in the dark web ecosystem. Based on our observations from analysis on dark web data using Lunar, we’ve identified the top 7 marketplaces on the dark web in 2025. We developed Lunar to monitor the deep and dark web, including dark web marketplace sites. Most dark web marketplaces use cryptocurrencies like Bitcoin for transactions to help maintain anonymity. Once a buyer makes a payment, it’s usually held in escrow until they receive what they bought. For those venturing to the shadier side of the web or those who just want to know their identity is safe, dark web monitoring tools and identity theft protection are a must-have.
No longer restricted to dial-up, many of us now consider access to a stable high-speed internet connection a critical element of our daily lives. We pay our bills online, check our bank statements, communicate via email, find information, and maintain a presence on social media. Track and analyze darknet activities using our advanced cyber threat intelligence platform to stay ahead of emerging threats. While this topic may seem distant for most people, understanding how these spaces operate is crucial. It helps us stay more vigilant, better protect ourselves, and make informed decisions online. Fake marketplaces and scams thrive on the dark web because there’s no one to turn to if you get scammed.
Tips For Safe Browsing

Each layer ensures your IP address remains hidden, offering a degree of anonymity unparalleled on the surface web. However, this also means that navigating the dark web can be slower due to the extensive encryption involved. The dark web often conjures images of clandestine meetings and shadowy transactions.
Navigating Darknet Market Links Safely
Tor Metrics highlights that about 22% of daily Tor users come from Russia, while the USA ranks second at 15%. Tor has around 2 million daily users exploring over 65,000 onion sites. Riseup is available on the surface web, but its presence on the Tor network extends its privacy benefits by letting you use its services without exposing their real-world identities.
Impreza Hosting is a service that helps you host a site on the Tor network. It provides an .onion URL and an interface for you to manage your Tor site easily. It also boasts that no personal information is required to use the service, and payment can be made with cryptocurrency. Keybase also offers extremely user-friendly secure chat and file-sharing services through its app.
- Nowadays, many people use the Tor browser to surf the public internet and navigate the deeper parts anonymously.
- Moreover, the layers of encryption and the bounce of your data from node to node effectively mask your IP address, enabling online anonymity.
- The Hidden Wiki plays a crucial role by listing verified onion links, warning users about scams, and giving descriptions to help them make informed choices.
- Freenet is still an experiment designed to resist denial-of-service attacks and censorship.
Best Practices For Finding Onion Sites
These services form the communication backbone for sensitive conversations in high-risk environments. The dark web hosts a variety of content, including forums, illicit marketplaces, and educational resources. While some sites facilitate illegal activities, others provide valuable information for journalists, activists, and researchers.
Microsoft Warns About New Variant Of XCSSET Malware On MacOS
- Defunct services and those accessed by deprecated V2 addresses are marked.
- Again, we can’t emphasize enough that security and anonymity are paramount to those on dark websites.
- Afterwards, your request will be matched with the appropriate website.
- Dark.fail’s clean interface and commitment to regular updates make it an excellent choice for users seeking safer navigation of the dark web.
- Radar Rundown Private search engines use the metasearch or proxy search model and the proprietary cr…
- Unlike the surface and deep web, you can’t access the dark web via a standard or specialized search engine.
To provide freedom of speech and keep journalism a strong pillar of the economy, the BBC made this Tor mirror. It helps people anonymously use the BBC website without restrictions. The famous social media platform has a prominent presence on the dark web. However, we do not advise readers to log onto this dark web mirror site; doing so would risk their privacy and that of others. When you try to enter a .onion website, it will reroute your access request around the internet, bouncing it off three random servers before you reach the target website.

Stay Up-to-date With KELA News And Insights
Tails never writes anything to the computer’s hard drive, running only from the RAM of the computer, which is wiped clean when the computer is shut down. Check around with other users and ask if they know anything about the new marketplace. These high levels of anonymity increase the opportunity for the “bad guys” to sell drugs, stolen IDs, credit cards, weapons, and many more compromised products or information.
It has built a reputation for being a reliable source of stolen credit card data and PII. Renowned for its extensive inventory of financial data and sophisticated operating methods, Brian’s Club is a key player in the underground economy of financial cybercrime. To expand their reach, some marketplaces established parallel channels on Telegram. This further complicates monitoring efforts because now you need to search for the related Telegram channels and track activity there and on the marketplace itself.
It publishes news in English and other major languages like Italian and Spanish. The advantage of this version is that you can effectively create a Facebook account anonymously or use this social media platform in a restricted region. Consequently, you’ll have maximum privacy while sharing opinions and anti-oppression resources.
The dark web version of Facebook isn’t malicious, but if you log into it, it will keep your data. Think of this as a hub for information on just about anything you’re looking for, regardless of the topic — yes, even juicy conspiracy theories. On Hidden Wiki, you can find working links to sites like ProPublica, Facebook, Deep Web Radio, and more. With each random server, your traffic bounces off, and a layer of encryption gets added.
The dark web is a playground for hackers, cybercriminals, and people with nefarious objectives. We strongly advise you against visiting it, even if your intentions are good. Though the dark web offers anonymity for journalists and activists in oppressive regimes, it raises many ethical concerns. Cryptocurrency is the primary payment method, making transactions irreversible and nearly impossible to trace. Tor, I2P, and Freenet are three common technologies that make up the dark web.
You can head over to Archive Today to look at snapshots taken by other users. Alternatively, you can take a snapshot of a web page that you consider important and want to ensure is archived for freedom of information purposes. The great thing about sharing via the Dark Web on SecureDrop is that users can do so without fear of persecution and without the possibility of being tracked down and punished.
Fortunately, in Hidden Wiki, every website is followed by a brief description so that the user knows what to expect. You can also take a look at the blogs & essays section if you want to find some nifty coding resources. Well, VPN over Tor is basically its opposite – instead of going through the VPN first, the signal passes through the Tor network, before going through the VPN. Next step – your request will be transferred to Tor entry nod which in turn transfers to one or more Tor relays. Afterwards, your request will be matched with the appropriate website.



